Goals
The typical goals of the security engineering activity are to:
- Address Threats.
Understand and prepare to combat security threats including malicious:- Access, copying, destruction, disinformation, distribution, interference with, misappropriation, modification, replacement, repudiation, theft, and use of confidential information (e.g., personal information, financial information, propriatary information, trade secrets, military intelligence).
- Acess, destruction, modification, replacement, theft, and use of hardware components.
- Access, interference with, and theft of services (e.g., computer time, cable television, telephone service).
- Protect Threatened Assets.
Protect threatened assets including:- Information (data components).
- Software components.
- Hardware components.
- Personnel components.
- Meet Relevant Standards.
Meet or exceed all relevant security standards (e.g., organizational standards, national laws) by taking due care and performing due diligence. - Limit Losses.
Thereby avoid, reduce, and eliminate actual losses (or the risk of loss) due to security breaches, whereby the loss can be:- Personal, organizational, or national
- Economic, military, political, or social
Objectives
The typical objectives of the security engineering activity are to:
- Assess the risks to the endeavor and its work products.
- Produce and maintain the endeavor’s security policies.
- Assess the effectiveness of the security policies.
- Enforce the security policies:
- Ensure that the security requirements are reused, elicited, analyzed, and specified.
- Ensure that the security architectural mechanisms are properly implemented.
Examples
Examples of the security engineering activity include engineering the security of a:
-
Endeavors:
- Business enterprise
- Program of related projects.
- Project
- Work Products:
Preconditions
Security engineering typically may begin when the following preconditions hold:
- The security team is adequately staffed and trained.
Completion Criteria
Security engineering is typically complete when the following postconditions hold:
- Retirement of threatened assets.
- Completion of the retirement phase.
Tasks
The security engineering activity typically involves the following producers performing the following tasks:
- Security Team, which performs:
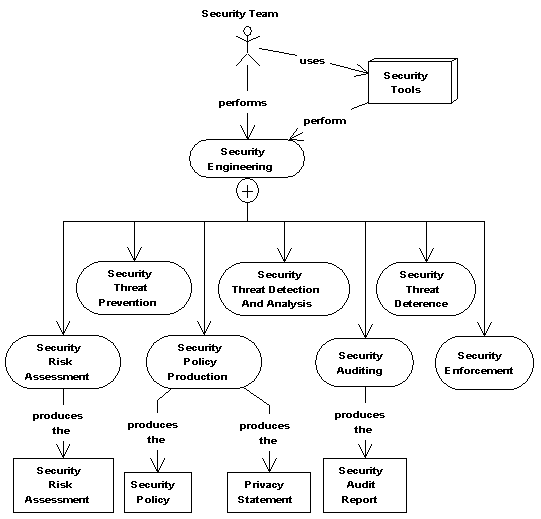
As you can see in the following figure, security engineering
is performed by the security team using security tools. It
consists of seven tasks, the performance of which produces the
four security work products.
Environments
Security engineering is typically performed using the following environment(s) and associated tools:
Work Products
The security engineering activity typically results in the production of the following work products:
Phases
The security engineering activity tasks are typically
performed individual phases as documented in the following
table:
Guidelines
- Security engineering is closely related to the following
other activities:
-
Requirements Engineering,
during which security requirements are elicited, analyzed, specified, and managed. -
Architecting,
during which common security mechanisms are identified and selected. -
Testing,
during which security testing occurs. -
Quality Engineering,
during which security processes and work products are evaluated. -
Risk Management,
during which security risks (among others) are identified, analyzed, documented, monitored, avoided, and mitigated. -
Disaster Recovery,
during which potential security-related disasters (among others) are analyzed, avoided, prepared for, responded to.
-
Requirements Engineering,
- The sources of security threats can be:
- Individuals:
- Hackers, who breach security for the thrill of it (e.g., denial of service, vandalism, sabotage, website defacement)
- Crackers (e.g., thieves and other criminals), who breach security for profit (e.g., theft, embezzlement, consumer fraud, blackmail, stalking and harrassment, pornography)
- Disgruntled current and former employees, who breach security for revenge
- Industrial and governmental spies (theft of trade secrets and intellectual property)
- Terrorists (e.g., sabotage, infowarfare
- Organizations:
- Competiing businesses (theft of trade secrets and intellectual property)
- Domestic and foreign governments
- Domestic and foreign military organizations
- Organized crime organizations
- Terrorist organizations
- Individuals:
- The preconditions of this activity should be the union of the preconditions of its constituent tasks.
- The completion criteria for this activity should be the union of the postconditions of its constituent tasks.